Is SSH TCP or UDP Understanding SSH Protocol Basics
Is SSH TCP or UDP?
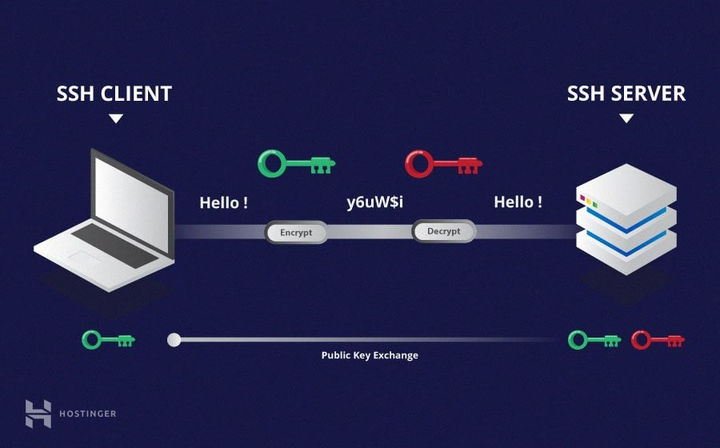
When working with SSH (Secure Shell), a common question arises: Is SSH TCP or UDP? The answer is straightforward: SSH uses TCP (Transmission Control Protocol). Here’s why TCP is the preferred choice for SSH and how it ensures secure and reliable communication.
Why SSH Uses TCP
- Reliability: TCP ensures data packets are delivered in the correct order and without errors. This is crucial for SSH, which relies on accurate data transmission for secure operations.
- Connection-Oriented: TCP establishes a stable connection between the client and server before data transfer begins, making it ideal for SSH sessions.
- Error Checking: TCP includes built-in error detection and correction, ensuring data integrity during SSH communication.
- Security: SSH is designed for secure remote access, and TCP’s reliability complements its encryption and authentication mechanisms.
Why Not UDP?
UDP (User Datagram Protocol) is faster but lacks the reliability and error-checking features of TCP. Since SSH prioritizes security and accuracy over speed, UDP is not suitable for SSH communication.
How SSH Works with TCP
- Port 22: By default, SSH operates on TCP port 22. This port is used for establishing secure connections between the client and server.
- Handshake Process: SSH uses a TCP handshake to establish a connection, followed by encryption and authentication to secure the session.
- Data Transfer: Once the connection is established, SSH encrypts all data transmitted over the TCP connection, ensuring privacy and security.
Key Takeaways
- SSH uses TCP for reliable and secure communication.
- TCP’s error-checking and connection-oriented nature make it ideal for SSH.
- SSH operates on TCP port 22 by default.
- UDP is not used for SSH due to its lack of reliability and error-checking.
Conclusion
SSH relies on TCP to provide a secure and reliable method for remote access and data transfer. Understanding this fundamental aspect of SSH helps you appreciate why TCP is the backbone of secure communication in networking. If you found this post helpful, share it with others!